In most companies, SMEs included, cybersecurity is still reduced to an arsenal of technologies, procedures and awareness training. On the cyber communication side, the crisis team is in place and trained, messages and statements are ready — sometimes even personalised. Everyone is on high alert, scanning for any sign of attack… while still having to keep the business running.
Meanwhile, cyber threats are accelerating — more sophisticated, more stealthy, automated, and supercharged by AI. The result: a vicious circle. The business leader becomes the hamster in the cyber wheel. And when an attack succeeds, the usual culprit is singled out: “human error.” A weak password. A careless click. A missed procedure.
The error is analysed. The process is reinforced. The employee involved is, at best, sent back for another cyber training. At worst, they are blamed — with the threat of dismissal for gross misconduct.
👉 The good news? There are concrete solutions — but only if we look beyond technical tools and put people and communication back at the very heart of resilience.
👉 What if we took a step back?
Avec ce sommaire :
- The machine has swallowed the human and social space
- What the Big Consultancies Say
- The blind spots of tech-centric cyber governance
- The benefits of another approach
- Our way forward
The machine has swallowed the human and social space
Let’s look at the work environment we’ve built over decades, in the name of profit and efficiency.
- Dashboards saturated with KPIs.
- Support desks drowned in chatbots.
- Complaints and orders reduced to online forms.
- Emotions and opinions scrutinized on social networks.
In short, the machine has absorbed the human and social space. ☝️Yet people are still people—made of emotions, relationships, and a need for recognition. And a company is still a social structure aimed at creating value—ideally durable and useful to society.
🤔Still, when a cyberattack succeeds, we point the finger at people…
- who are asked to be ever more productive,
- whose needs are dissected through surveys, analysis, figures,
- from whom human contact is removed,
- and from whom we nevertheless demand flawless cyber vigilance.
🧷 A few uncomfortable questions
How can you ask your teams to stay focused, creative, and vigilant when they already work under constant pressure—deadlines, margins, and fear of layoffs?
How do you bring customers and partners into a cyber-resilience collaboration if your exchanges are reduced to KPIs and online platforms?
How do you convince investors of your cyber leadership if your relationship with them is limited to financial and strategy reports?
How can you expect fair media coverage during an attack if you don’t know the journalistic landscape (your sector, region, cybersecurity beat) and only reach out when you need them?
What the Big Consultancies Say
EY – Wellbeing (2023): 35% of UK employees say they are more stressed than two years ago. Stress, anxiety and depression account for 12.8 million lost workdays every year in the UK. 🔗 [EY Wellbeing Report PDF]
👉 How can we expect vigilance and sound judgment under such conditions?
Fortinet – Security Awareness Report (2024): Nearly 70% of organizations recognize that their employees lack fundamental security awareness. Many respond with awareness and training programs, scheduling monthly or quarterly campaigns. Leaders generally report these trainings improve security posture. 🔗 [Fortinet Report 2024]
👉 But beyond technical knowledge, what about stress management, fear of making mistakes, or confidence in voicing doubts?
👉 Fatigue and inertia effects: the study itself notes dissatisfaction among some participants — lack of engaging content, no guidance on how to make training feel like real support rather than a constraint.
👉 No measurement of psychological or social impact: the report does not examine working conditions, fear of sanctions, or company culture that enables (or blocks) error reporting without fear. It identifies a “lack of awareness,” but not the reasons why awareness is missing.
👉 Biased answers: 86% of managers say they are satisfied with training programs. But that’s management’s view, not employees’. On the ground, risky behaviors persist — proof that between theory and real life under pressure, there is a gap technocentric governance cannot fix.
WEF – The Cyber Resilience Compass (2025): The WEF’s compass puts the human factor at the heart of cyber resilience through four key pathways: leadership, people & culture, ecosystem engagement, and business processes. It emphasizes building trust through open communication, moving away from technical jargon, fostering accountability and psychological safety, developing external cyber communication strategies, and mapping dependencies upstream and downstream with external stakeholders. 🔗 [WEF Cyber Resilience Compass 2025 PDF]
👉 Positive point: this approach does not focus only on technology but also considers organisational dimensions. Limitation: its view of psychological safety remains centered on incident reporting and feedback mechanisms. The lived emotional reality of employees and their social relationships are still left out.
The Blind Spots of Tech-Centric Cybersecurity Governance
Cybersecurity governance has been built around tools, processes and technical controls: firewalls, patch management, SOCs, crisis response plans. Essential, yes.
But by focusing only on the machinery of defense, we ignore a whole part of the equation: the human dynamics.
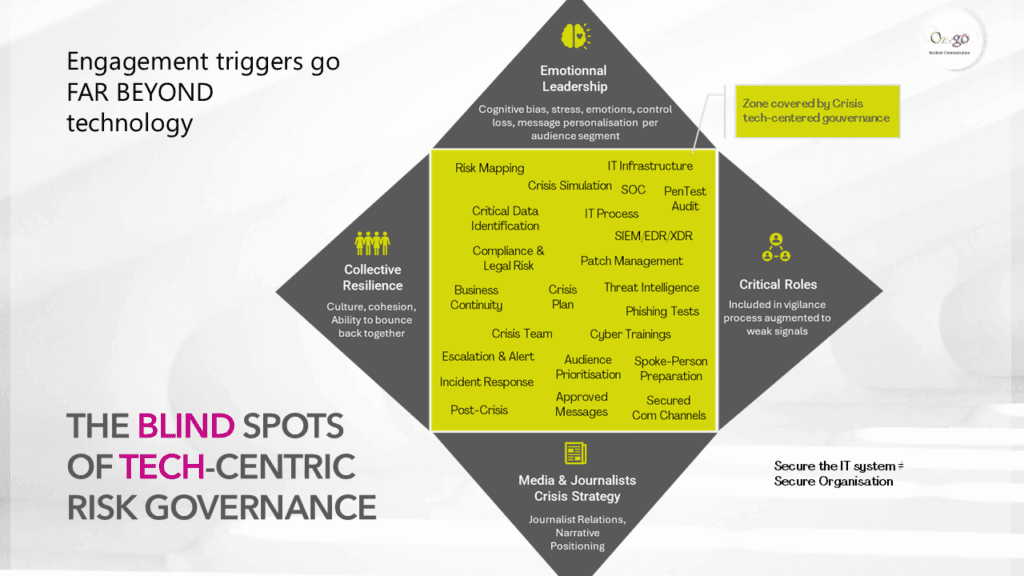
What tech-centric governance fails to account for:
- Psychological factors: stress, cognitive overload, cognitive biases, layoff anxiety, persistent fatigue, burnout — all of which erode, distort or weaken vigilance.
👉 The real issue isn’t just training or procedure; it’s the organization’s ability to protect mental health and build a durable climate of trust—recognized on a par with financial KPIs. - Emotional factors: shame, guilt, lack of confidence, feelings of uselessness or lack of recognition, fear of being judged — which all suppress error or anomaly reporting.
👉 The answer isn’t a crisis-comms kit alone; communication must create a space where error becomes learning, where raising a doubt is valued, and where speech is freed from fear of blame. - Social factors: loneliness, loss of meaning, the sense of being “just a cog,” and the erosion of human bonds inside teams and with clients/suppliers—replaced by impersonal platforms and KPIs.
👉 Re-weaving these bonds—restoring the collective and the relational—underpins resilience communication, which safeguards performance and trust alike. - Communication factors: silos, constant top-down, standardized messaging, and no real culture of open, transparent, continuous exchange.
👉 Shift from reactive communication to living, inclusive, horizontal communication—that’s where collective vigilance happens: everyone becomes an actor and amplifier of resilience, not a mere executor.
In other words, tech-centric cybersecurity strengthens the technical shield but leaves wide open the human, emotional and social blind spots — precisely where so many vulnerabilities take root.
The Real Benefits of Another Approach
Putting people and communication at the heart of resilience already means gaining in competitiveness, responsiveness and performance.
Our Way Forward
We are not here to replace technology — but to complete it. Our mission: help SMEs widen their vision to include what is too often forgotten — cyber communication as the backbone of resilience.
- Augmented crisis communication: not just pre-written messages and media training for a spokesperson, but the building of strong internal and external bonds.
- Resilience governance: define your vision of cyber resilience, identify the levers and barriers to cohesion, integrate fatigue, stress and trust into KPIs, and establish a hybrid committee to steer and coordinate.
- Resilience communication: develop and deploy a long-term communication strategy that fosters and sustains cohesion, engagement and collective reflexes across the company’s ecosystem.
👉 Securing IT is not enough. Securing people — through communication — is just as vital.







