What Resilient Communication is
Resilient Communication is a proactive crisis communication that focused on long-term preparedness, learning and adptability to strengthen responses to turbulences.
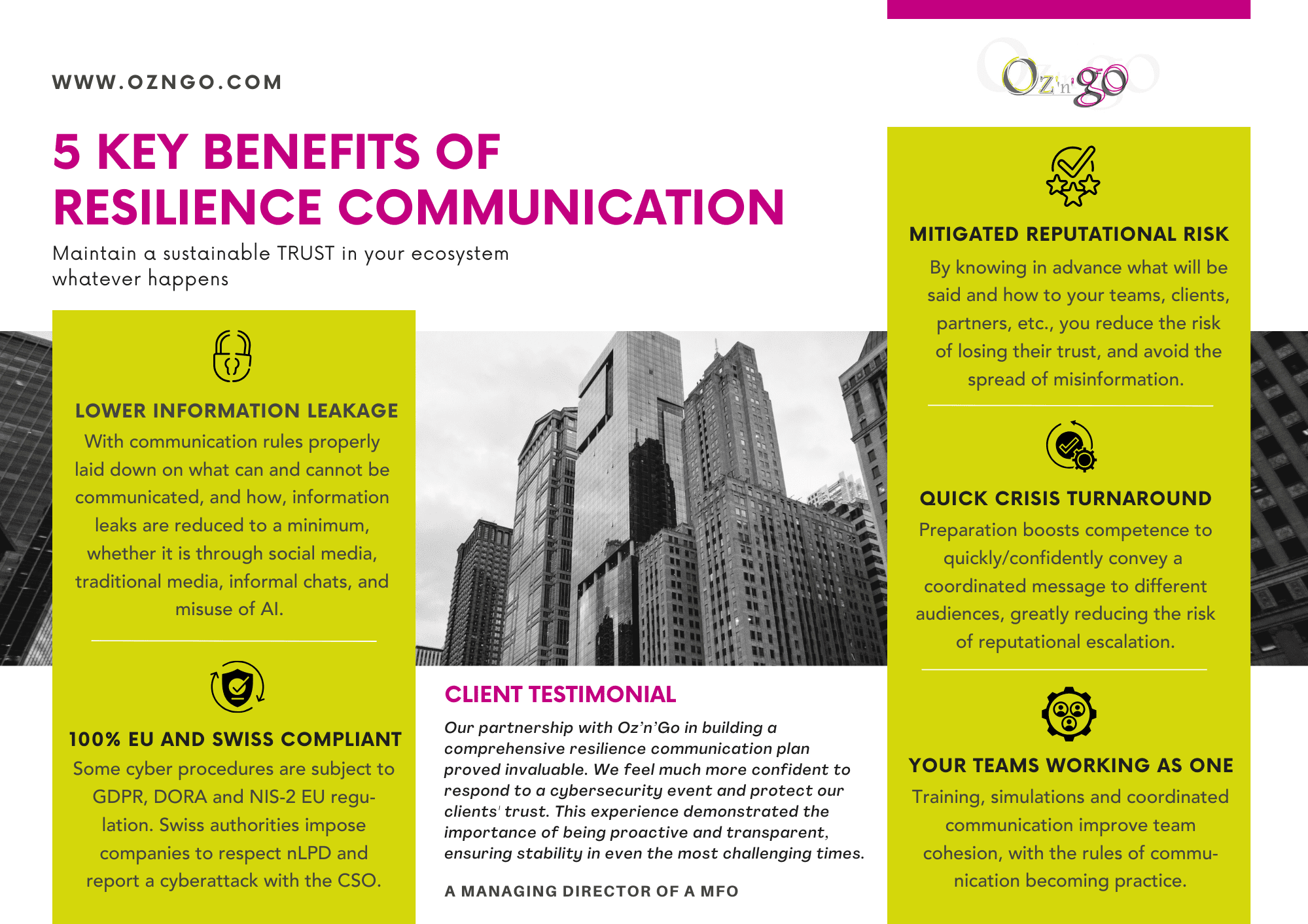
Goal: Maintain a sustainable Trust within an organisation’s ecosystem by preparing an organisation and its stakeholders for future challenges and crises, including cyberattacks.
Objective: keep the narrative under control whatever happens with a tested and trained crisis communication structure in place (team, scenarios, training and simulation, messages and documents, secured communication channels, processes and protocoles, etc.)
2/3 weeks to protect your Reputation on the long run
Resilient Communication Overview
5 Core Elements
The resilient communication strategy and plan are based on the risk assessment results, which describe the threats, the company’s crown jewels (vital sensitive data), its strengths and weaknesses, as well as the priorities to focus on.
The goal is to build a risk-based communication framework before a crisis occurs and beyond, tailored and enhanced to address various potential challenges over time.
It starts by building a Crisis Management Team we coach to develop the Crisis Management Plan aimed at defining and setting up all the procedures and measures to respond to identified attack or crisis (ripple effect incl.), and restore the normal operations as quickly as possible.
Oz’n’gO developed a unique methodology (Risk Criticality Assessment – RCA) to map the roles from the most to the least at risk. It helps setup and adjust an AI-generated Zero-Trust architecture, refine IAM (Identity Access Management) and SIEM (Security Information and Event Management).
The communication framework covers an internal and external segmented strategy and plan that define and setup tailored communication protocoles, the secured communication channels, the security DOs and the DON’Ts, ready-to-use material, etc.

- We put at your disposal templates, checklists, and assessment questionnaires
- We guide you how to gain internal and external stakeholders’ engagement
- We liaise with top experts (cybersecurity, legal expert, insurance expert, white hackers, etc.)
ENISA (European Union Agency for Cybersecurity) set up an online test SMEs can use to measure where their organisation stands in terms of cybersecurity.
Role criticality Assessment
Our Role Criticality Assessment (RCA) is a unique methodology to fine-tune and personalise your crisis management strategy.
Knowing your most sensitive data (crown jewels), we define WHO in your organisation is processing WHAT DATA, WHEN and HOW, according to the threats identified and compared to the (cyber)security awareness and competence of the people concerned.
The principle
Oz’n’GO mapping methodology is based on the following:
- the sensibility of the data processed at which critical step
- the type of cyber-attacks identified
- the level of knowledge/awareness of the people processing the most sensitive data at the critical steps
- the ethical and legal framework
We guide you in our 5-step process
with checklists, templates, pre-built questionnaires, etc.
Our tool combines the different data collected to produce a fine map of the different roles/positions
from the most to the least at risk,
at each step of the sensitive data processing.
Three benefits
- You know exactly where to focus your efforts (people, procedures, protocoles and processes), WHEN and HOW
- You tailor your support services and training program
- You create synergies between members and teams
Machine Learning is Human… and personalised
The very first step before thinking of cybersecurity training is to go through a simulation test, which unveils the areas of improvements from a technical, legal and behavioural perspective. Three types of simulation can be delivered.
Real-life Cyber War Games and Simulations are scenario-based exercises that mimic real-world cyber attacks. They can range from simple phishing attacks to complex, multi-stage intrusions.
Simulations in real-life conditions allow to test the limits of the management team in terms of stress endurance and the capacity of communicating clearly and effectively without conveying anxiety and worry.
The communication processes, technologies, and procedures are analysed and measured. The vulnerabilities are identified and grasped.
3 Types of Simulations
Red Team (attackers) simulates a cyber attack while the Blue Team (defenders) works to thwart the attack. It helps to refine defense tactics and strategies.
Discussion-based sessions where participants walk through different cyber attack scenarios and discuss their responses. It helps to identify gaps in policies and procedures.
It involves comprehensive hands-on exercises where participants are using real tools and techniques to defend against simulated attacks. This is the most realistic training.
By cross-checking the results of the simulation and the RCA’s ones, a personalised training program can be defined between cybersecurity-oriented, communication-specific and behavioural training courses.
- Cyber Awareness Training (general and role-specific) to educate people on cybersecurity principles (password manangement, phishing awareness, safe internet, AI use, etc.).
- Crisis communication Training
- Stress management
- Time management
- Change management
- Remote Work best-practices
- a Deep–Dive media training to
teach and train the spokesperson on responding to challenging questions and negative publicity. (message development, posture and body language, interview techniques, mock interviews)
- a Light (social) media training to teach the employees how to stay vigilant on tricky information requests by media, the best practices of social media during a crisis, etc.

Specific cyber-training courses
We contribute to cyber-training programs designed to equip teams with the knowledge and skills needed to defend against cyber-attacks.
Program to guide senior top managers on their risk management strategy.
- What risks are acceptable?
- Who is the most at risk in the organisation?
- What process should be changed and how?
- Am I compliant with the cybersecurity laws?
- What impact on my company insurance?
It provides advanced skills on cybersecurity.
PenTesting, Incident Response, Network Security, Malware Analysis, Vulnerability Scanning.
Our experts can deliver solutions, techniques and best-practices.
Quick build cybersecurity skills through intensive training.
Security foundations, threats and vulnerabilities, network defence, and penetration testing.
Learn the technical and legal cybersecurity framework.
Discover our Success Stories
COMING SOON